New Golang malware runs Monero miner on servers
Image credit: QuoteInspector
A new strand of Golang malware discovered this week installs the well-known Monero cryptocurrency miner, XMRig on infected servers.
The wormable malware exploits popular vulnerabilities such as an RCE (Remote Code Execution) flaw in Oracle WebLogic tracked as CVE-2020-14882.
Scans network for vulnerable services
This week, researchers at Intezer have revealed a new strand of Golang malware that exploits different vulnerabilities on both Linux and Windows servers to eventually turn them into Monero (XMR) miners.
“The attack uses three files: a dropper script (bash or powershell), a Golang binary worm, and an XMRig Miner—all of which are hosted on the same C&C,” explained Intezer security researcher Avigayil Mechtinger.
To began its exploitation activities, the malware scans the network for open ports in a TCP SYN attack. The list of services (and ports) it targets includes Apache Tomcat and Jenkins (8080), MySQL (3306), and WebLogic (7001).
Once it finds one or more of these open ports, the worm starts brute-forcing these, such as by trying commonly used username-password combinations and exploit payloads, to gain further access to vulnerable systems, and to spread itself.

“Post exploitation, the malware will deliver a loader script: ld.sh for Linux and ld.ps1 for Windows. The loader is responsible for dropping and running the XMRig Miner and the Golang worm on the exploited service,” explains Mechtinger.
Malware has a low detection rate
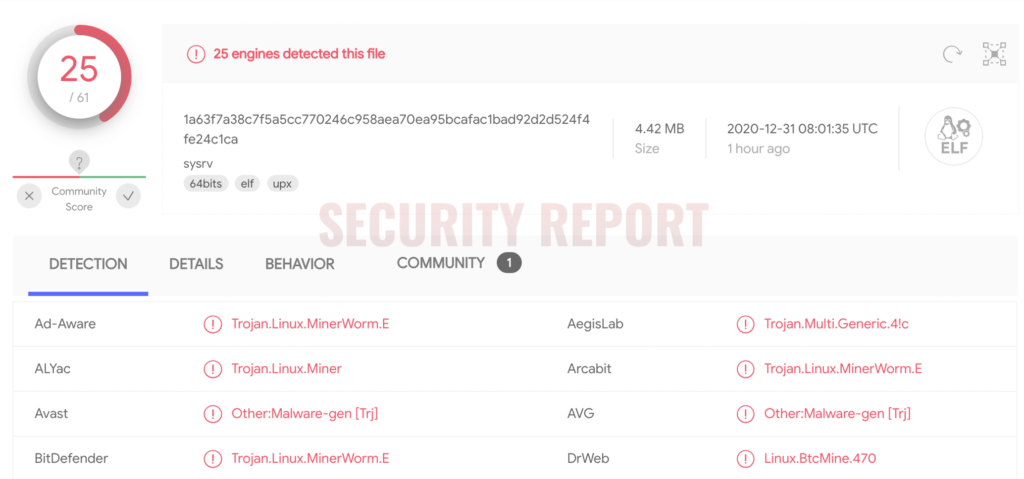
At the time of Intezer’s analysis, the malware had zero detection rate, according to VirusTotal.
By comparison, the same sample is now being detected by over 40% of the antivirus engines today, as observed by Security Report.
“In 2020, we saw a noticeable trend of Golang malware targeting different platforms, including Windows, Linux, Mac and Android. We assess with high confidence that this will continue in 2021,” reads Intezer’s post.
The fact that the worm has identical code for both its PE and ELF variants, with the latter having been undetected in VirusTotal for long is an indication of ongoing evasive Linux threads that fly under the radar of most security products.
Intezer’s detailed research findings have been provided in their blog post. Joakim Kennedy has also been thanked by the company for his contribution to the research.

 Rogue WordPress plugin: Threat hunters uncover credit card skimming campaign targeting e-commerce sites
Rogue WordPress plugin: Threat hunters uncover credit card skimming campaign targeting e-commerce sites  Carbanak Banking Malware Resurfaces with Updated Tactics in Ransomware Attacks
Carbanak Banking Malware Resurfaces with Updated Tactics in Ransomware Attacks 




