Insomnia Cookies exposes database passwords, then quietly fixes the leak
American bakery company remembered sweetly for its late-night warm cookie trucks and shops on college campuses was caught leaking sensitive data on its website.
American bakery company sweetly remembered for its late-night warm cookie trucks across college campuses was caught leaking sensitive data on its website.
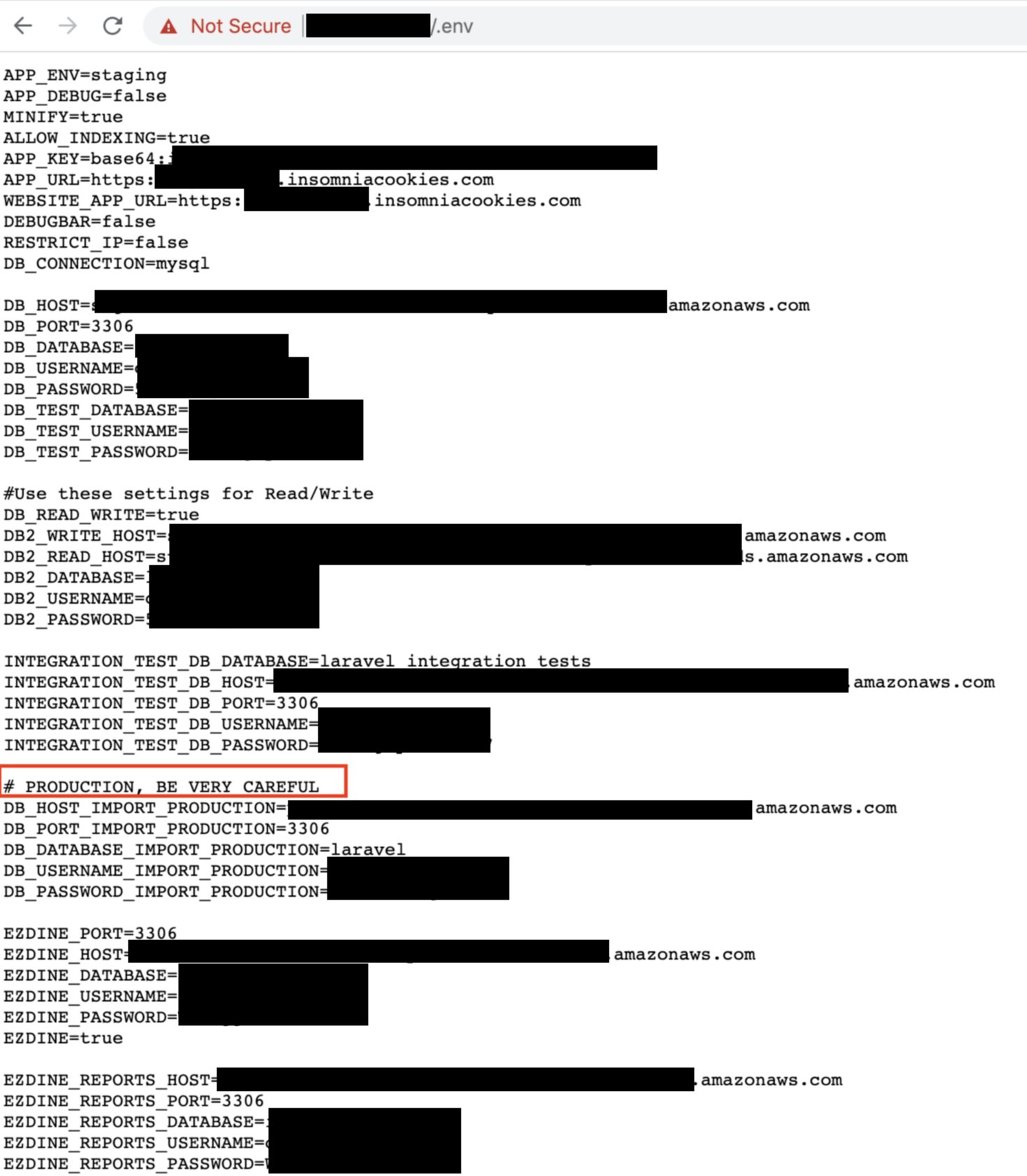
The data exposed via public .env files included production server database credentials, including the DB server addresses, ports, usernames, passwords, and API keys.
.env files contain sensitive configuration data such as environment variables, API keys, passwords, and are supposed to remain private, hidden from prying eyes of the public.
The exposed .env file provided enough information for an attacker to potentially be able to access the Insomnia Cookies database and carry all sorts of attacks, such as dropping entire databases, or illicitly obtaining the information contained within them, such as customer data.
Bob Diachenko, Cyber Threat Intelligence researcher who discovered the flaw on November 12th via public IoT search engines (such as Shodan), responsibly reported it to Insomnia Cookies.
However, Diachenko didn’t receive a response. And it seems, Insomnia Cookies quietly patched the flaw following Diachenko’s report.
“Insomnia Cookies left almost all of their prod credentials exposed via publicly accessible dot-env file on one of its IPs (indexed by all IoT search engines). Silently secured after responsible disclosure, no response,” tweeted Diachenko.
Diachenko told Security Report he had discovered the data leak last week via public IoT search engines and immediately reported it to Insomnia Cookies:
“I discovered that one on Nov 12th and immediately sent alert to IC.”
“Basically, dot-env is environment variables file for internal usage only. Developers define here settings for databases and endpoints so if you have this, most of the company’s infrastructure is compromised,” Diachenko told Security Report.
When building and publishing websites to production environment, it may be wise to check file permissions, to prevent data leaks such as this one.
Security Report has reached out to Insomnia Cookies for comment but haven’t heard back yet.


