Bug bounty programs don’t always pay up: researchers
It is worth noting that critical exploits could sell on the darknet for far worth more than what a nominal bounty payout may entail. Earlier this year, a Zoom zero-day exploit was being sold for $500,000.

Bug bounty platforms have filled a genuine need by connecting security researchers and pen-testers with products vendors in a manner that promotes security awareness, collaboration, and provides monetary incentives for vulnerability reporters.
But they are not without their issues.
This week I reported on BleepingComputer how a bug bounty reporter had plagiarised an exploit originally posted by researcher Guido Vranken, and walked away with a cash award via Monero’s HackerOne bug bounty program.
It wasn’t until later that the original reporter had noticed the incident, which is when Monero confirmed that the bug report had indeed been stolen.
But, even in clear cut cases where plagiarism isn’t an issue, bug bounty platforms have recently earned a reputation for not always paying up even when legitimate security vulnerabilities are reported by the researchers.
Actually, it is rather the product vendors running these bounty programs on platforms that bear the responsibility of paying bounty awards.
But, because the entire reporting workflow and communications are handled via platforms like HackerOne and Bugcrowd, it is not hard to see why many researchers may place blame where it may not belong.
Guido Vranken, whose exploit had been stolen mentioned to me in passing:
“HackerOne (or rather its programs) have gotten a reputation for not paying out rewards (for valid submissions), which is a distinct issue [than plagiarism] but it might interest you to research and report on that.”
We don’t pay for this, but we’ll fix this
Complaints from multiple security researchers finding that bug bounty programs often fall short of their promises when it comes to paying out bounties have surfaced in recent times.
A security researcher from a Fortune 500 company who prefers to remain anonymous told Security Report News:
“I did come across some other researchers posts claiming the same issue where their older report was ignored and thereafter exact same issue(s) were accepted months/years later when reported by others.”
“Another thing I have noticed is that HackerOne staff and vendor representatives try to downplay valid reports and fix the vulnerabilities silently but deny bounties. This has happened to me a few times and I am pretty sure it has happened to others as well,” they continued.
“Only when disclosure is requested, do they accept the report or issue a rightful-bounty. It’s a sad but true reality,” concluded the researcher.
Stories of other researchers that share this frustration of bug bounty programs applying their policies inconsistently have also been posted on Twitter in the past:
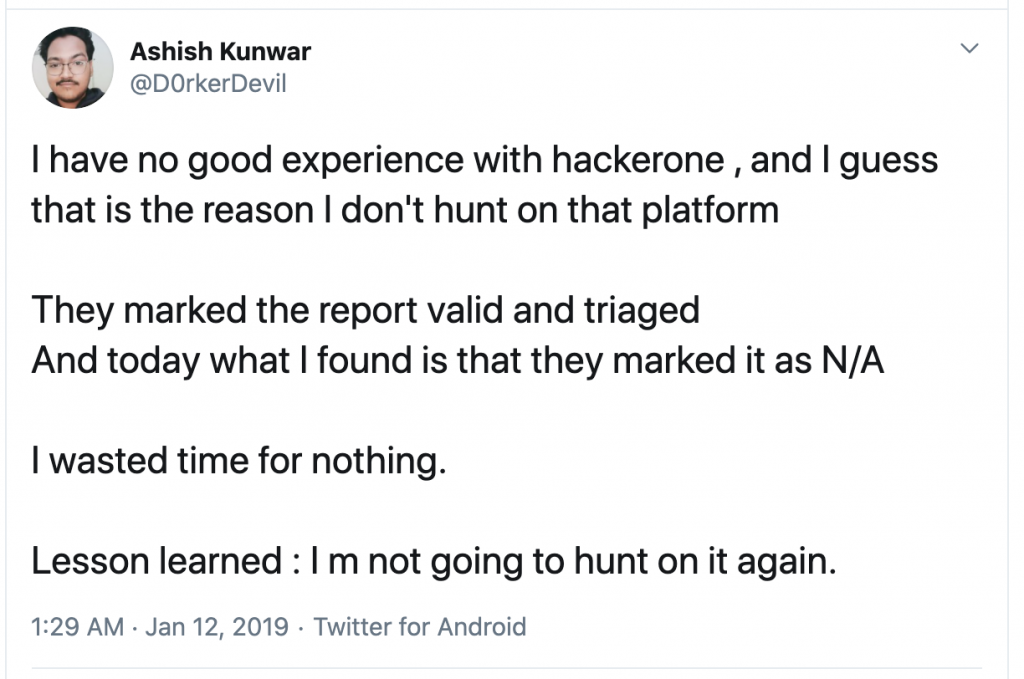
Source: Twitter
Another researcher who goes by the name Yumi had posted in 2018, how their previously filed HackerOne report was dismissed as “informative.”
Shortly, however, the company had silently patched the reported vulnerability.
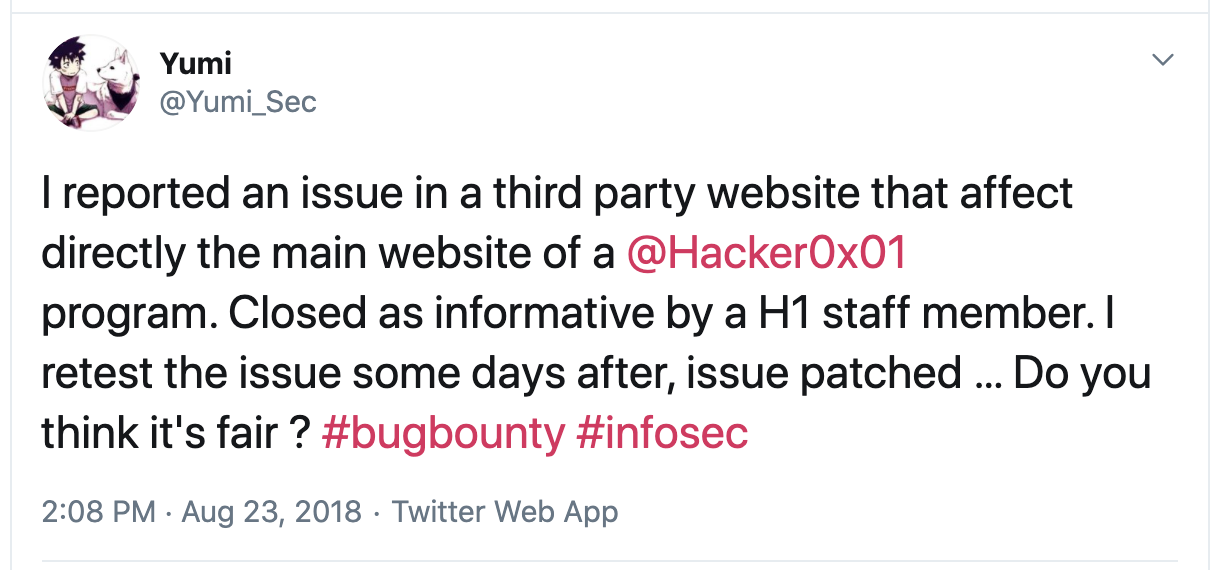
Source: Twitter
Cases of companies trying to downplay the severity of reported vulnerabilities, or negotiating down the reward payouts are hardly surprising.
A recent example is, Slack paying a nominal $1,750 reward to a researcher who had spent significant effort on reporting a vulnerability.
When asked about the inconsistent payment scenarios with regards to bounties, a HackerOne spokesperson provided Security Report News with some insights:
“While I can’t speak to these vulnerabilities specifically, there are many reasons a report would be closed as informative or not applicable. At its core, ‘informative’ means a report contains useful information but doesn’t warrant an immediate action or a fix.”
“A program can consider providing an alternative risk assessment or other mitigating factors, and public disclosure is available with mutual agreement.”
“‘Not applicable’ means the report doesn’t contain a valid issue and/or has no security implications. The customer has the final say on each vulnerability, but we advise customers to follow an industry-standard CVSS rating and create explicit direction for hackers on their program page to reflect their focus.”
“You can read more about [what the] report states here. If there is ever a disagreement both hackers and customers can request mediation from HackerOne,” the spokesperson told Security Report News.
The detail shared by HackerOne is helpful indeed in clarifying what constitutes terms like Informative and Not Applicable in this context.
However, unless policies on validating the authenticity of vulnerability reports and on bug bounty payouts are reviewed and made more consistent, researchers are likely to explore other avenues for making their discoveries public, if not ignore responsible disclosure guidelines altogether.
It is worth noting that critical exploits could sell on the darknet for far worth more than what a nominal bounty payout may entail. Earlier this year, a Zoom zero-day exploit was being sold for $500,000.


