NETGEAR routers vulnerable to “root” code execution, no patch yet

In a recently released vulnerability disclosure from d4rkn3ss from VNPT ISC as well as Adam Nichols of GRIMM, we learn of an unpatched vulnerability impacting at least 79 NETGEAR router models that can let an attacker execute code with “root” privileges.
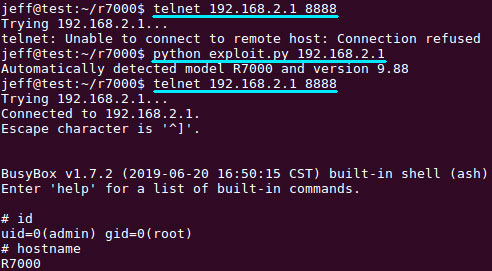
Nichols downloaded NETGEAR firmware from their website and began decompiling it using disassemblers and analysis tools like Hex-Rays.
The researcher was able to quickly figure out, browsing through the web server’s code in the firm, that certain variables, such as user_input were vulnerable to an overflow.
“After the call to read_content (the recv helper function), the parser does some error checking, combines the received content with any previously received content, and then looks for the strings name="mtenFWUpload" and "\r\n\r\n" in the user input,” states the disclosure.
“If the user input contains these strings, the rest of the user input after these strings is passed to the abCheckBoardID function. Grepping the firmware’s root file system, we can see that the string mtenFWUpload is referenced from the files www/UPG_upgrade.htm and www/Modem_upgrade.htm, and thus we can conclude that this is part of the router’s upgrade functionality.”
While most modern devices have protection technologies like “stack canaries”, ASLR and DEP to protect against code execution, should a buffer overflow exploit succeed, this isn’t the case for select NetGear models.
“In most modern software, this vulnerability would be unexploitable. Modern software typically contains stack cookies which would prevent exploitation. However, the R7000 does not use stack cookies. In fact, of all of the Netgear products which share a common codebase, only the D8500 firmware version 1.0.3.29 and the R6300v2 firmware versions 1.0.4.12-1.0.4.20 use stack cookies. However, later versions of the D8500 and R6300v2 stopped using stack cookies, making this vulnerability once again exploitable. This is just one more example of how SOHO device security has fallen behind as compared to other modern software.”
Nichols has provided a proof-of-concept (exploit) for the vulnerability.
The same vulnerability was also disclosed on Zero Day Initiative (ZDI) by d4rkn3ss from VNPT ISC and has been assigned the identifier, ZDI-CAN-9703 while a CVE assignment is pending.
While 79 models of NetGear routers remain unpatched, the disclosures of this vulnerability did not follow the standard guidelines, reads the ZDI advisory:
“Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service to trusted machines. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. This could be accomplished in a number of ways, most notably with firewall rules/whitelisting.”
A list of 79 router models that are vulnerable is as follows:
| AC1450 | MBR1516 | WGR614v9 |
| D6220 | MBRN3000 | WGR614v10 |
| D6300 | MVBR1210C | WGT624v4 |
| D6400 | R4500 | WN2500RP |
| D7000v2 | R6200 | WN2500RPv2 |
| D8500 | R6200v2 | WN3000RP |
| DC112A | R6250 | WN3100RP |
| DGN2200 | R6300 | WN3500RP |
| DGN2200v4 | R6300v2 | WNCE3001 |
| DGN2200M | R6400 | WNDR3300 |
| DGND3700 | R6400v2 | WNDR3300v2 |
| EX3700 | R6700 | WNDR3400 |
| EX3800 | R6700v3 | WNDR3400v2 |
| EX3920 | R6900 | WNDR3400v3 |
| EX6000 | R6900P | WNDR3700v3 |
| EX6100 | R7000 | WNDR4000 |
| EX6120 | R7000P | WNDR4500 |
| EX6130 | R7100LG | WNDR4500v2 |
| EX6150 | R7300 | WNR834Bv2 |
| EX6200 | R7850 | WNR1000v3 |
| EX6920 | R7900 | WNR2000v2 |
| EX7000 | R8000 | WNR3500 |
| LG2200D | R8300 | WNR3500v2 |
| MBM621 | R8500 | WNR3500L |
| MBR624GU | RS400 | WNR3500Lv2 |
| MBR1200 | WGR614v8 | XR300 |
| MBR1515 |
At this time, it is not known when will a patch be released.


