21,000 U.S. driver licenses up for sale on hacker forum after data breach
Over 21,000 U.S. driver licenses are being sold on a hacker forum, along with thousands of credit reports.

Photo by Quintin Gellar on <a href="https://www.pexels.com/photo/teal-volkswagen-beetle-631522/" rel="nofollow">Pexels.com</a>
A threat actor has put up over 21,000 U.S. driver licenses for sale on a hacker forum after a data breach.
The seller also told Security Report that they had over 2,000 credit reports and credit application forms containing sensitive customer information, such as names, dates of birth, SSNs, addresses, credit history, and vehicle purchase information.
These documents were allegedly obtained from a vulnerable server belonging to a lending company.
Update: added statement below from the lending company who has, thus far, not found any evidence of data breach.
Thousands of U.S. driver licenses, SSNs, credit reports stolen
This week, a threat actor has put up copies of over 21,000 Californian driver licenses for sale on a hacker forum. These copies were allegedly stolen from an online lending, identity verification, and finance solutions company.
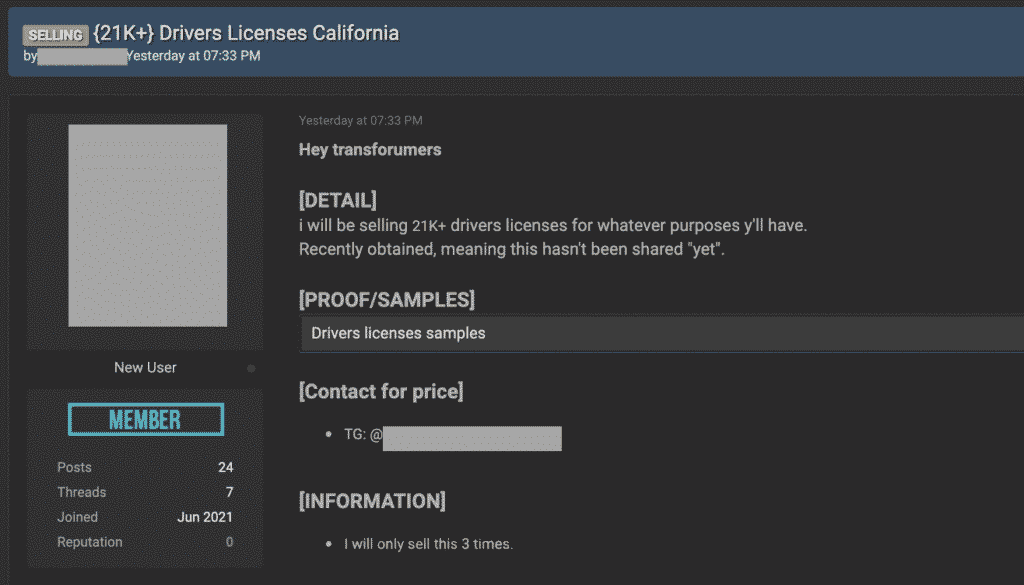
The seller who goes by alias Janus666 told Security Report that they had exactly 21,230 driver licenses, and 2,118 credit reports available for sale, obtained from a server they managed to breach sometime last week.
The credit reports/credit application forms expose sensitive information including customer names, dates of birth, SSNs, addresses, credit history, and vehicle purchase information.
While a majority of the driver licenses and credit reports are associated with residents of California, a small number of samples shared with us represent U.S. residents of some other regions as well.
“The drivers licenses are mostly of California, however there are some [from] Washington, Illinois, Arizona, Florida, Iowa, Nebraska, Minnesota, Michigan, Mexico*, Georgia, Colorado, Nevada, New Jersey, New York, Ohio, Pennsylvania, Texas, Tennessee. But these are in small numbers,” the seller told Security Report.
(*It isn’t clear if the threat actor meant “New Mexico” or Mexico)
Alon Gal, co-founder, and CTO of cybercrime intelligence firm Hudson Rock, who had first spotted and tweeted about this forum post said stolen driver license data could be abused by adversaries looking to conduct different kinds of frauds and identity theft.
The seller told Security Report, although they hadn’t set a fixed price on the data set, they did manage to sell driver licenses at least once, charging $400 for 10,000 copies.
Security Report also reviewed the sample set of Californian driver licenses posted by the seller on the forum. After researching public records, we observed that the details in the licenses represented real persons.
California Department of Motor Vehicles (DMV) did not respond to our request for comment when asked if the department will take any steps to notify the impacted drivers.
Documents allegedly stolen from a lending company
Security Report attempted to trace the source of this data breach, and how were these files obtained by the threat actor.
Although the threat actor did not comment on what vulnerability or weakness was exploited to obtain the credit reports and driver’s licenses, they claim that eLEND Solutions is the company where they obtained these files from. Furthermore, these files were allegedly uploaded by car dealerships across the U.S. to eLEND’s systems.
The copies of stolen credit reports seen by Security Report have URLs printed on the footer of every page and start with extranet.dealercentric.com:
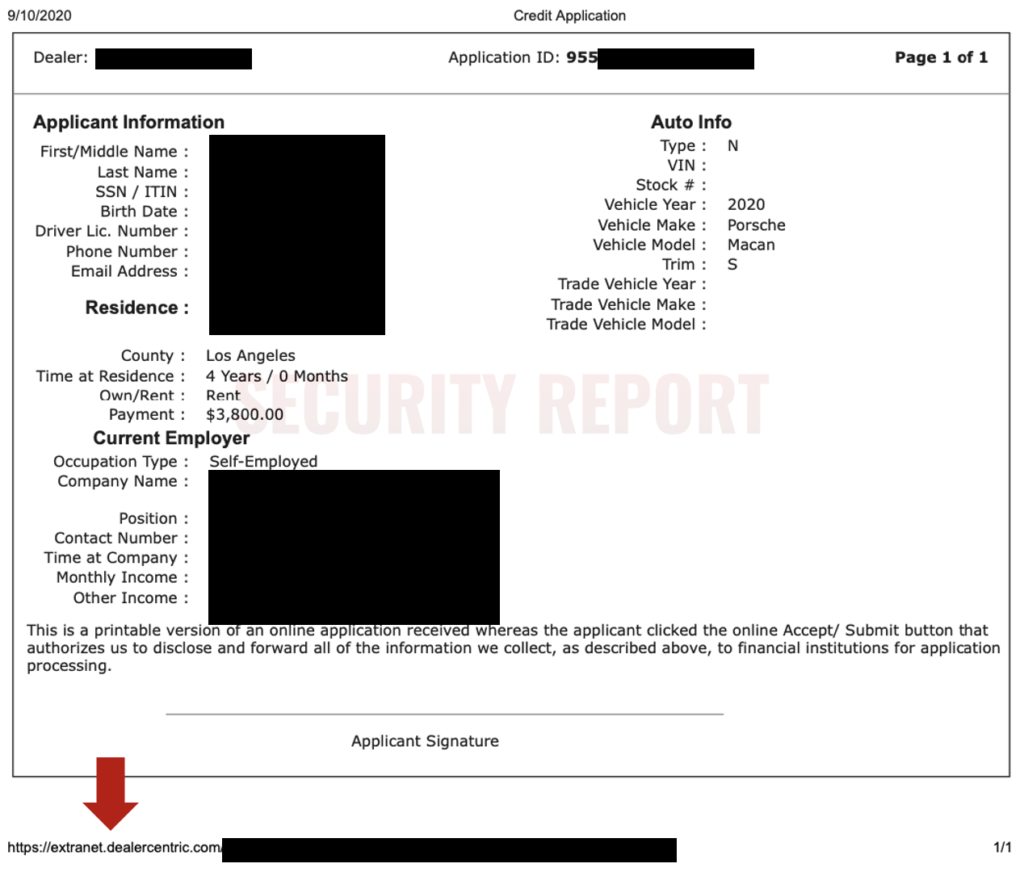
Although this domain belongs to eLEND Solutions, a trading name of DealerCentric Solutions Inc., at the time of our testing, the specific URLs that were expected to lead to credit reports, instead prompted us with a login screen before granting access. This indicates any improper authorization flaw, should it have existed, is now patched.
Security Report repeatedly reached out to eLEND well in advance for comment but we did not hear back. As such, the source of this data breach remains unconfirmed.
Update – 27-July-2021, eLEND’s IT department has responded with a statement:
When we checked the five purported sample licenses from the download link, I was unable to locate any of these names/license numbers in our system in the past 7 years. We have not been contacted by any threat actor for ransom or otherwise. In addition, the images appear vastly different than the ones we capture using the ID-150 scanner, casting additional doubt on the claims.
According to the reported threat, they claim to have retrieved the images via “an eLEND website” without specifying any details. Our corporate site is fully isolated from any of our data, so it is not possible to have retrieved anything from there. Regarding our platform site, It is not possible to access any data without first authenticating as a valid dealer user via multi-factor authentication. The scope of access is further restricted to the user’s roles and the dealer’s pool of data, making it extremely unlikely that this claim has any validity.
We have not been alerted by our intrusion detection systems of any suspicious activity, so the likelihood of this being a breach of any other kind is highly unlikely as well.
We have initiated an investigation and will advise with any findings once complete; however, at this point in time we are seeing no signs that this is a legitimate claim.
– eLEND’s IT department spokesperson


